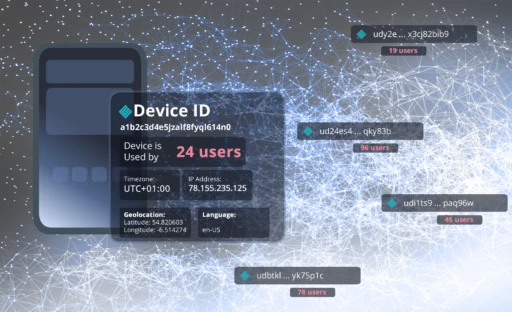
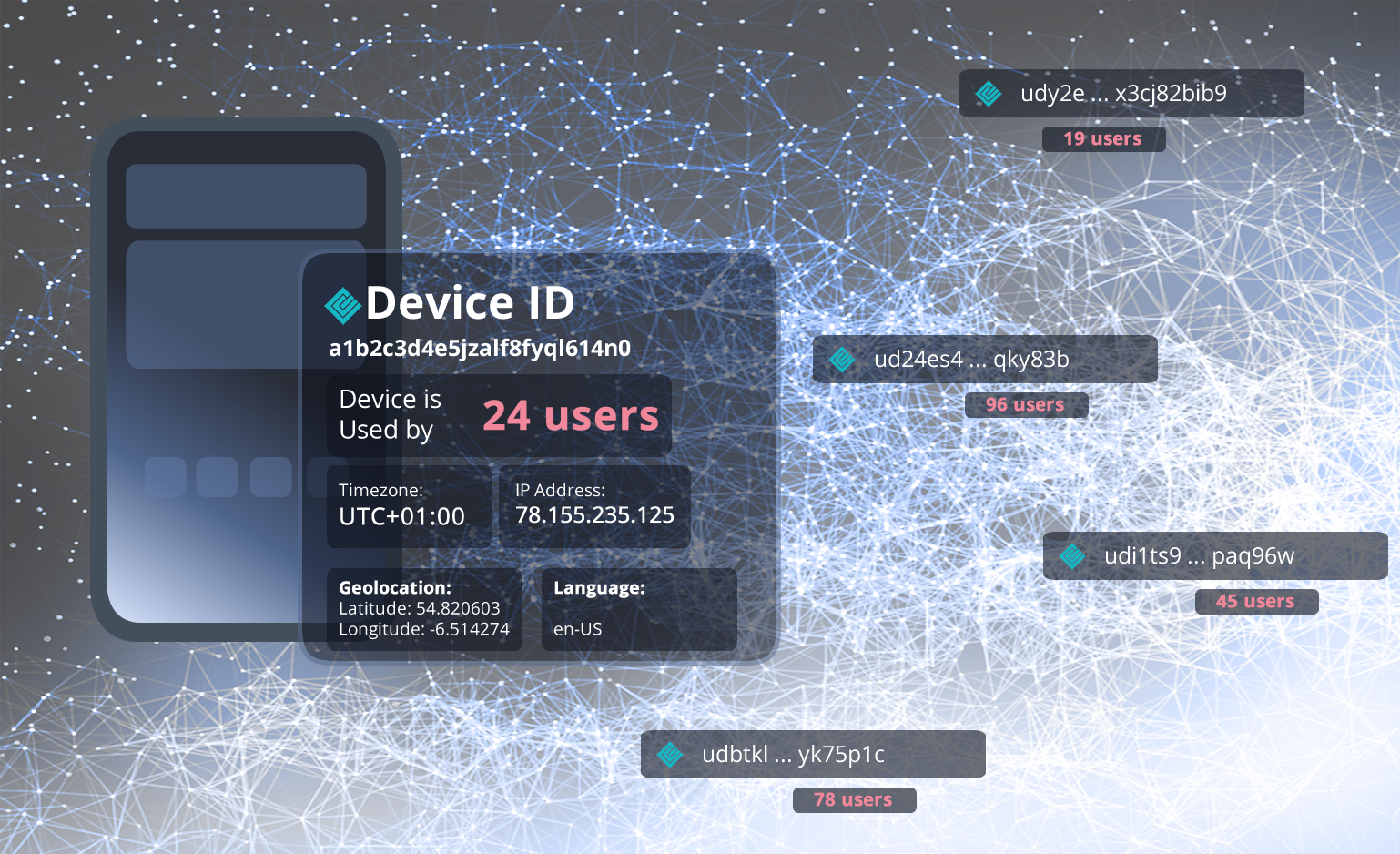
A Concrete Example to Get Started
Imagine this scenario: A user regularly accesses a web application – always from the same laptop, at the same time of day, and with similar behavior patterns.
Suddenly, there’s a login from an unknown device, with unusual behavior patterns, and at an atypical time.
Conventional security systems would potentially allow this access as long as the username and password are correct.
Not so with the PaperOffice Device Fingerprint API: Our technology immediately detects the deviation from the usual pattern and requests additional security verifications – even before sensitive data is compromised.
This precision is exactly what makes the difference between a potential data breach and a secure system.
What Exactly Is a Device Fingerprint?
A device fingerprint is comparable to a digital fingerprint of your device. Unlike traditional cookie-based methods, it captures a variety of device properties and environmental variables to create a unique identification – without storing data on the user’s device.
At PaperOffice, we have perfected this technology over two decades. For more than 20 years, we have been developing and refining our own API and have now made this proven solution available to other companies as well.
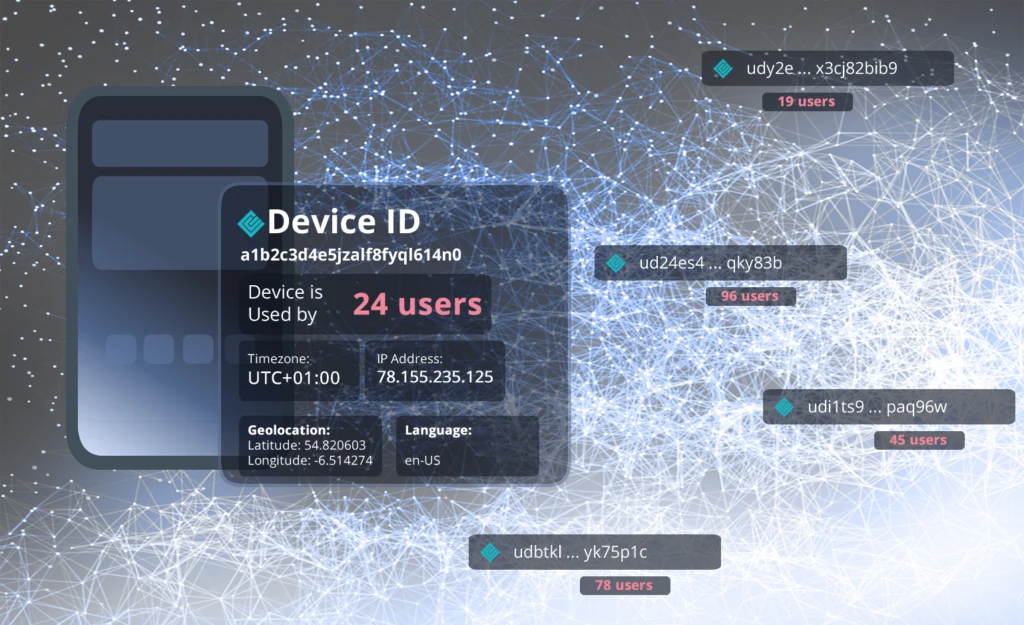
Our Device Fingerprint API is a standalone product that can be used independently of our other solutions such as PaperOffice DMS.
Unlike many competitors who rely on third-party technologies, our solution is completely based on proprietary technology.
The Measurable Advantages of PaperOffice Device Fingerprinting
The numbers speak for themselves:
- 99.8% detection rate for suspicious access attempts
- 96% reduction in fraud attempts for customers who have implemented our technology
- Response time under 50ms even under high server load
- 5x improvement in fraud detection compared to conventional cookie-based approaches

These results are no coincidence, but the result of decades of development and continuous optimization of our technology in our state-of-the-art data centers in Navarra.
How Does Device Fingerprinting Work at PaperOffice?
Our approach is based on a holistic capture of device properties:
1. Hardware-Based Identification
We capture precise hardware characteristics without invading privacy:
- Processor characteristics: Not just the CPU type, but also specific performance features and utilization patterns
- Memory usage: Characteristic patterns of RAM usage
- Graphics system: Detailed information about the graphics hardware and its capabilities
- Screen configuration: Resolution, color depth, and multi-monitor setups
2. Software Profile with Deep Analysis
The software environment reveals much about the authenticity of an access:
- Operating system details: Not just version, but also specific configurations and update status
- Browser fingerprinting: Analysis of over 50 different browser properties
- Plugin landscape: Patterns of installed extensions and their versions
- Language preferences: Detailed analysis of regional and language settings
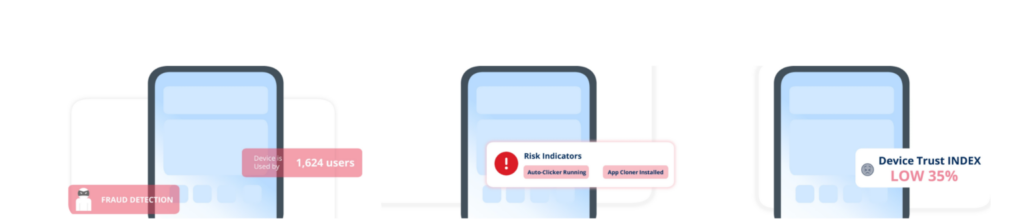
3. Advanced Network Analysis
Our cluster infrastructure enables a particularly deep network analysis:
- Connection characteristics: Analysis of network latency, packet loss, and throughput rates
- Routing signatures: Detection of unusual routing paths indicating proxies or VPNs
- TLS fingerprinting: Analysis of TLS handshake characteristics
- High-precision geo-localization: Up to 10 times more accurate than conventional IP-based methods
Real-World Use Cases: Success Stories from Our Customers
Financial Service Provider Reduces Fraud Attempts by 94%
A medium-sized financial service provider implemented our Device Fingerprinting technology after repeatedly falling victim to account takeovers.
The result: Within three months, successful fraud attempts decreased by 94%, while customer satisfaction increased as legitimate users were affected by fewer security queries.
Government Agency Protects Sensitive Data from Unauthorized Access
A public administration uses our Device Fingerprint API to protect access to their internal systems.
When an employee attempted to access the administrative system from an unauthorized home device, our technology immediately recognized the discrepancy and prevented access – even before a human administrator had to intervene.
E-Commerce Platform Increases Conversion Rate by 18%
An online retailer used our technology to reduce fraud cases while improving user-friendliness.
By precisely distinguishing between legitimate and suspicious accesses, the retailer was able to reduce security requirements for known devices and recorded an increase in conversion rate of 18%.
The Technical Superiority of the PaperOffice Solution
Our implementation stands out in several key areas from the competition:
High-Performance Cluster Architecture
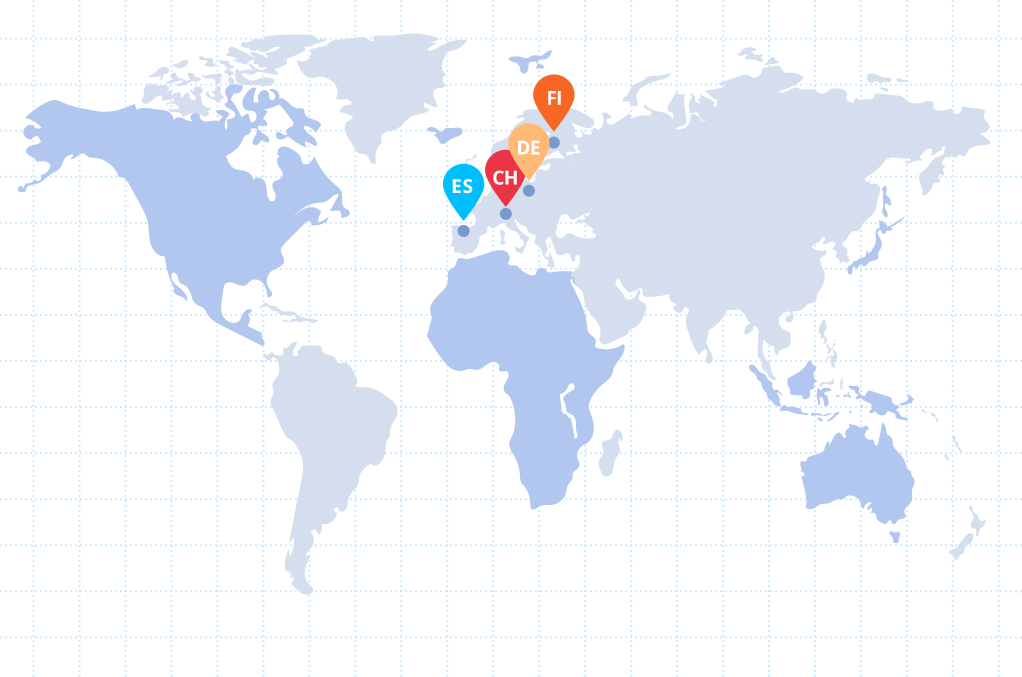
Our device fingerprinting technology runs on our powerful cluster infrastructure in Navarra:
Four dedicated API clusters (C1-C4) with 5 high-performance servers each High-performance GPUs such as RTX 4090 and RTX 3090 TI for AI-powered analytics Multiple redundant internet connections with 1 GBIT speed Uninterruptible power supply through Ecoflow Delta Pro systems
Innovative Cache-First Strategy
Our unique cache-first strategy enables lightning-fast results:
- Redis-based multi-level caching architecture with up to 100GB RAM cache
- Ramdisk optimization for temporary files with automatic purging
- Intelligent data replication between local and central caches
- 20-second synchronization intervals for maximum data freshness
Seamless Integration into Your Existing Infrastructure
Integrating our Device Fingerprinting API is remarkably simple:
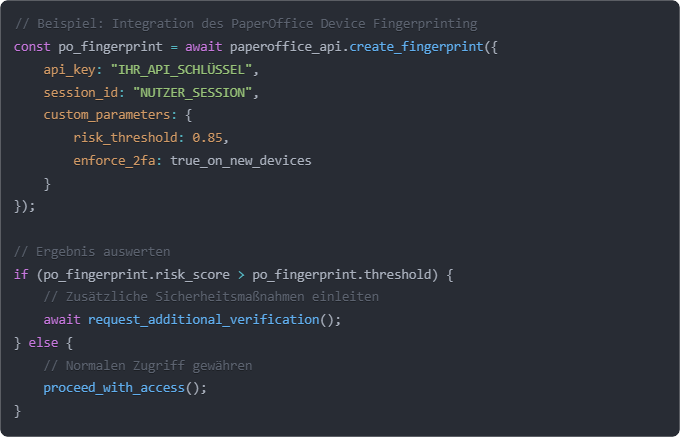
Integration requires minimal modifications to your existing code and offers maximum security.
Data Protection as a Central Design Principle
At PaperOffice, data protection comes first. Our Device Fingerprinting solution was developed from the ground up with data protection as a central design principle:
- No storage of personal data as part of the fingerprint
- End-to-end encryption of all captured information
- Strict data minimization according to GDPR principles
- Transparent documentation of all collected data points
- Regular external security audits and penetration tests

The Expert Opinion
Dr. Elena Martinez, renowned IT security expert, on our solution:
“PaperOffice’s Device Fingerprinting technology sets new standards in digital security. Particularly impressive is the balance between highest security and excellent user-friendliness – an area where many competitors fail.”
Conclusion: The Future of Digital Security Starts Here
Device Fingerprinting is not just an additional security feature – it’s the foundation for truly secure digital systems in today’s interconnected age. As a technology company with years of experience, PaperOffice has perfected this technology.
For over 20 years, we have been using our own API, based on the highest precision and efficiency. Now we are making this proven technology available to others to provide you with the most accurate results – because we don’t rely on third-party data, but develop and operate our own technology.
The continuous development of our Device Fingerprinting technology is part of our effort to always stay at the forefront of security and AI technology and to offer our customers the most secure and efficient solution on the market.
Experience the PaperOffice Device Fingerprint API difference – where maximum security meets outstanding user-friendliness.
I am a dedicated content writer at PaperOffice, specializing in creating insightful articles about document management and automation. With a focus on simplifying complex topics.