In today’s increasingly digitalized world, cyber attacks have become a daily threat to businesses. To protect your company and its sensitive data, it is crucial to take proactive measures.
Access control is an essential component of any cybersecurity strategy, referring to the ability to control and manage access to data, systems, and resources within a company.

This control enables companies to ensure that only authorized users can access specific information, while unauthorized access is prevented.
Access controls include various measures such as password policies, user permissions, Role-Based Access Control (RBAC), Two-Factor Authentication (2FA), document and information location, and encryption.
In the world of cybersecurity, there are numerous providers that focus on theory and develop comprehensive concepts for defending against cyber attacks. However, there is often a lack of concrete countermeasures in the form of software solutions that implement this theory into practice.
Theory alone is not sufficient to effectively protect a company from cyber attacks.
Concrete, implementable solutions are needed to strengthen security infrastructure and identify and address potential vulnerabilities.
Risk Analysis and Assessment
The first step in implementing an effective cybersecurity strategy is conducting a comprehensive risk analysis and assessment.
This involves identifying potential threats and weaknesses in the company’s IT systems and infrastructure, as well as assessing the possible impact of a cyber attack on the business.
Implementation of Security Measures
Utilizing Document Management Systems to Strengthen Cybersecurity:
An effective and secure document management system like PaperOffice plays a crucial role in bolstering a company’s cybersecurity.
By integrating state-of-the-art security technologies, PaperOffice provides a comprehensive solution for protecting sensitive data and documents from cyber threats.
Encryption Technologies: PaperOffice utilizes advanced encryption technologies to ensure that all stored data and documents are protected from unauthorized access.
By encrypting data during transmission and storage, companies can rest assured that their confidential information is securely stored.
Access Control: With PaperOffice, companies can implement granular access controls to ensure that only authorized users can access specific documents and information.
Administrators can set individual access rights for users and restrict access to sensitive data based on user roles and permissions.
Revision-Secure Archiving: PaperOffice offers a revision-secure archiving feature that ensures all changes to documents can be logged and tracked.
This ensures the integrity and authenticity of stored data and enables companies to comply with regulatory requirements and meet audit demands.
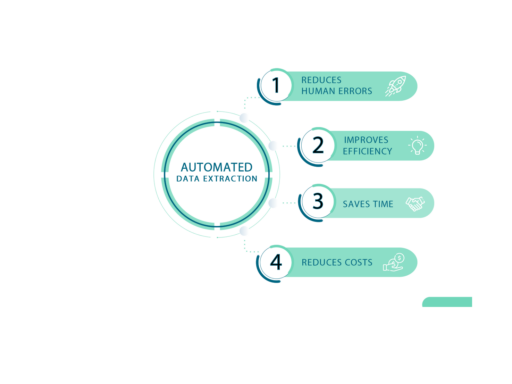
Automation of Security Processes: By automating security processes, companies can save time and resources while improving the efficiency of their security measures.
PaperOffice offers a variety of customizable automation features, including automatic classification and tagging of sensitive documents, automatic monitoring of document changes, and automatic notification of security incidents.
Integration with Other Security Tools: PaperOffice can seamlessly integrate with other security tools and solutions to support a holistic security strategy. By integrating with firewalls, Intrusion Detection Systems (IDS), and other security solutions, companies can strengthen their defense line and effectively protect against cyber threats.
Overall, PaperOffice provides a comprehensive solution for strengthening a company’s cybersecurity by combining state-of-the-art security technologies, granular access controls, revision-secure archiving, and automation of security processes.
With PaperOffice, companies can effectively protect their sensitive data and documents and defend against the growing threats from the cyberspace.
Continuous Monitoring and Updating
The cybersecurity landscape is constantly evolving, and therefore, it is important for companies to continuously monitor, update, and adapt their security measures.
This includes regularly updating software and operating systems, monitoring network activities, and conducting security audits.
For more information on how PaperOffice can secure your data and enhance your operational efficiency, visit www.paperoffice.com and discover the power of advanced AI-driven document management solutions.
PaperOffice Trial Version
Test the award-winning PaperOffice for 14 days without obligation at:
https://www.paperoffice.com
Social Media
Facebook: https://www.facebook.com/paperoffice.en
Twitter: https://twitter.com/PaperOffice_en
PaperOffice ComDesk
Find out more at:
https://help-en.paperoffice.com
YouTube
► http://www.youtube.com/c/PaperOfficeEN
PaperOffice Blog
https://blog-en.paperoffice.com
PaperOffice Guide
Scanners and Document Management: Benefits and Uses: TOP 15 Reasons for Using a DMS
I am a dedicated content writer at PaperOffice, specializing in creating insightful articles about document management and automation. With a focus on simplifying complex topics.